Life in a Post-Password World: Why Identity is the New Security Boundary
Bulletproof

IT security used to be relatively straightforward. Put up a solid firewall, have users password-protect their applications, and keep one eye on the controls just to be sure. It was just like home security — keep intruders out by putting a fence around the yard and locking the doors.
As digital intruders have become increasingly sophisticated, IT teams and vendors have worked hard to develop new protection and detection software and to impose stringent password requirements on users.
The new tools and rules effectively strengthen the fence and reinforce the door. But what happens when someone scales the fence and the key to the door is under the welcome mat? And what about this age of smartphones, mobile apps and workplace bring-your-own-device policies, where the challenge is further magnified because there simply are no fences?
In a digital world with shifting boundaries, there is only one way for IT teams to secure their systems: identity and access management that focuses on the person trying to cross the threshold.
Why Fences are Out of Vogue
At home, fences and locked doors are the basic tools that control access to our living space. When the risk of intruders is high, some people reinforce the perimeter with secondary locks or alarm systems that send signals to appointed gatekeepers when things go awry. However, at each step in the process, there is a common weakness: the person who holds the key.
Today, users have multiple keys—or passwords—that grant access to dozens of digital spaces. In the quest to keep those spaces secure, IT gatekeepers have installed advanced detection systems to monitor access and they’ve demanded better passwords to make it near-impossible for intruders to pick the virtual lock.
However, the burden of carrying those keys is heavy, even when the weight is digital. As a result, many people tuck their passwords in convenient places, like on sticky notes in desk drawers, where they’re easily accessible by others. People also started reusing passwords for multiple accounts to make their collection easier to manage.
According to Gartner, the global research and advisory firm, compromised identity credentials continue to be a major element in data breaches. At the same time, IT security teams are overwhelmed by the number of alerts from detection systems that are designed to flag potential unauthorized entries, making it difficult to get beyond the noise and identify real problems.
How the bad actors are getting worse
As companies generate increasing amounts of valuable data, cybersecurity threats and the risk of breaches are also increasing, making IT security even harder to achieve.
“Every industry is a target now, from a ransomware perspective or a cybersecurity perspective,” says Chris Johnston, VP of Sales for Bulletproof in Canada.
With the proliferation of mobile devices and the shift to the cloud, digital rabble-rousers have many more doors to try, which means that building better fences isn’t the answer.
“We used to deal with perimeter controls,” Johnston explains. “The idea was to defend your house so that nobody could get in. That worked in the past because all your data was in the house.”
IT teams need different tools to make sure that only the right people are allowed to cross the threshold. Thankfully, that’s what Bulletproof does. Built as an IT security company nearly 20 years ago, the Bulletproof team has been on the front line of this evolution.
“The cloud has brought all kinds of value on the productivity side because you can access your data from anywhere in the world, on any device, as long as you have authentication to get in,” says Trevor Flynn, VP of Managed Services at Bulletproof. “But so can anyone else, if they have your credentials.”
Passwords are only as strong as the user behavior protecting them. How many times have you “changed” your password by tacking on a new number to the old one? Or simply given away your streaming video password to a friend who wanted to download the latest hot show?
According to a study by password manager LastPass, “95 percent of people share up to six passwords with others, including financial, business, social media and entertainment, despite the majority of people acknowledging that it’s risky.” In other words, users are making it easier for bad actors to guess passwords, or they’re simply giving them away.
Have we reached peak password?
From malware to phishing to man-in-the-middle attacks, Flynn says bad actors are stealing the keys to the kingdom. So, what’s an IT guru to do?
“We have to start from a breach mentality and assume that someone else has your user credentials,” he says.
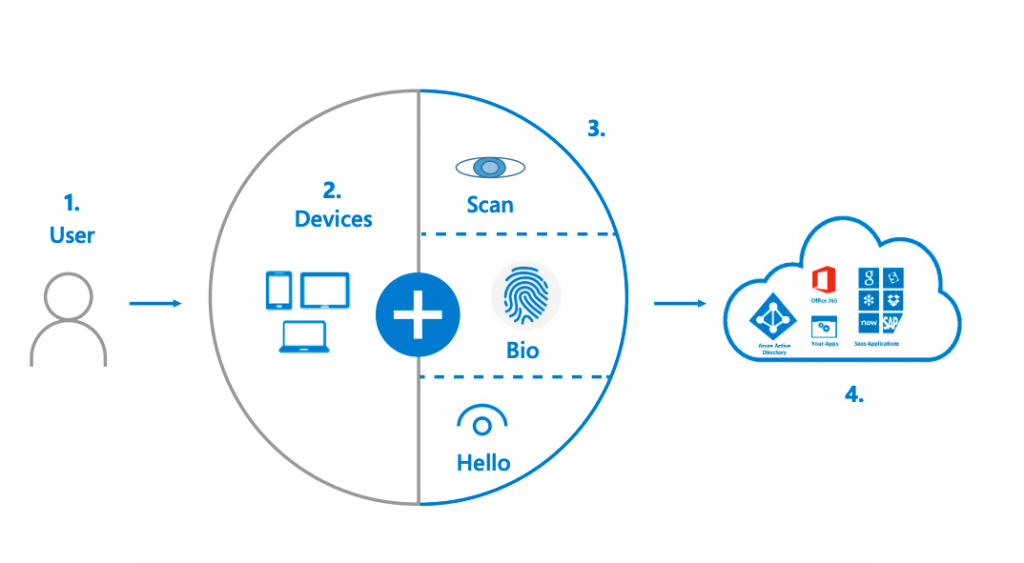
That sounds stark, but there is good news. Starting with multi-factor authentication, artificial intelligence, and machine learning, there is a whole suite of new identity and access management tools that IT security experts can deploy — all focused on validating the identity of the user.
While we might not yet live in a world without passwords, the trend is heading in that direction. Bio-metric verification, such as fingerprints and facial recognition, are increasingly used to supplement password access. Sophisticated algorithms can assess user login locations and access habits.
As a result of this shift, software powerhouses like Microsoft have necessarily turned themselves into security companies, and comprehensive security tools are now integrated into the Microsoft stack.
Building on its security pedigree, Bulletproof has leveraged these tools to elevate its offerings with Bulletproof 365 Enterprise (B365E), so that Microsoft-powered organizations can take full advantage of the built-in security features without having to develop and maintain in-house expertise in a demanding and ever-changing environment.
For more information about how Bulletproof can complement your IT security team, book a Security Workshop, or check out the Bulletproof 365 Enterprise Fact Sheet.
Read the original article here
Check out their profile on CollabHub here
.png?width=600&height=187&name=Untitled%20design%20(2).png)