3 Key Considerations for Password-less Protection
Bulletproof

3 Key Considerations for Password-less Protection
In our last post, we explored the future of passwords: getting rid of them entirely.
In this post, we’ll discuss 3 key considerations for moving toward password-less authentication.
The most critical step toward adopting a password-less strategy and getting users onboard is finding the right technology to power your security strategy.
With biometrics on mobile phones and computers becoming more ubiquitous, the number of password replacement technologies that the average user can access has increased.
As a Microsoft Gold Partner, Bulletproof has implemented many Microsoft solutions based on platform, hardware, or software that you can easily map with your password-less authentication requirements.
Key Consideration #1: Choosing the Right Password-less Authentication Technology
Introduced by Microsoft in Windows 10, Windows Hello uses biometric sensors or a PIN to verify a user’s identity. The Microsoft Authenticator app is a software token that allows users to verify their identity with a built-in biometric or a PIN when signing into their work or personal accounts from a mobile phone.
As a member of the FIDO Alliance, Microsoft has been working with other alliance members to develop open standards for the next generation of credentials. As a result, you can now use portable FIDO2 hardware devices to log into a work machine or cloud services on supported devices and browsers. Let’s go into more detail on each of these technology options.
Windows Hello for Business
Windows Hello for Business replaces passwords with strong MFA on Windows 10 platforms, including PCs and mobile devices. This authentication consists of a new type of user credential that’s linked to a device and uses a biometric or PIN. It lets you sign in with your face, iris scan, fingerprint, or a PIN, and lets you authenticate to enterprise applications, content, and resources without a password being stored on your device or in a network at all. The biometric data is only used locally and never leaves the device.
How it works:
The Windows Hello provisioning process generates a cryptographic key pair bound to the Trusted Platform Module (TPM) on a device. Access to these keys and obtaining a signature to validate user ownership of the private key is enabled only by the PIN or biometric gesture. The two-step verification completed upon enrollment creates a trusted relationship between the identity provider and the user. When a user makes the gesture through the device, the provider is able to verify the identity from the combination of Hello keys and the gesture. This activates an authentication token that allows Windows 10 to access resources and services.
Microsoft Authenticator App
The Microsoft Authenticator app enables users to verify their identity and authenticate to their work or personal account. Microsoft Authenticator can be used to augment a password with a one-time passcode or a push notification—or replace the need for a password entirely.
Instead of using a password, users confirm their identity through fingerprint scan, facial or iris recognition, or PIN. Built on secure technology similar to what Windows Hello uses, this tool is packaged into a simple mobile app, making it a convenient option for Android and iOS users.
How it works:
Instead of seeing a password prompt after entering a username, users get a push notification to verify presence. In the app, users confirm their presence by matching a number on the sign-in screen, then providing a face scan, fingerprint, or PIN to unlock the private key and complete the authentication. This multi-factor verification method is more secure than a password and more convenient than entering a password and a code. In some cases, it doesn’t require any typing at all!
FIDO2 Security Keys
FIDO2 is an evolution of the U2F open authentication standard based on public-key cryptography using hardware devices. This standard is intended to solve multiple user scenarios including strong first-factor (password-less) and multi-factor authentication.
With these new capabilities, a security key can entirely replace weak static username/password credentials with strong hardware-backed public/private-key credentials. These credentials cannot be reused, replayed, or shared across services. Devices and tokens that adhere to FIDO2, WebAuthN, and CTAP protocols enable a cross-platform solution of strong authentication without using passwords. Microsoft partners are working on a variety of security key form factors, such as USB security keys and NFC-enabled smart cards.
How it works:
Microsoft has been working with partners to enable strong password-less authentication by ensuring FIDO2 security devices work on Windows, the Microsoft Edge browser, and online Microsoft accounts.
For shared-device scenarios, security keys allow you to carry your credentials with you and safely authenticate to an Azure AD-joined Windows 10 device that’s part of your organization. You can use any shared Windows device belonging to your organization and authenticate securely without needing to enter a username and password. Unlike traditional passwords, these keys rely on high-security, public-key cryptography to provide strong authentication. Plus, these keys have all the benefits of a secured enclave to store credentials while also being portable—excellent news for deskless and kiosk workers.
Comparing Microsoft Technologies For Password-less Authentication
Here are some factors for you to consider when choosing Microsoft password-less technology:
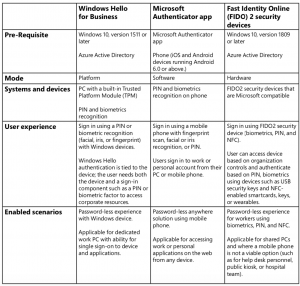
Key Consideration #2: Understanding How Strong Authentication Works
All three technologies use the same proven cryptographic authentication pattern, with credentials based on the certificate or asymmetrical key pair. These credentials—plus the token that is obtained using the credential—are bound to the device (Windows or FIDO2 device, or mobile phone). The authenticator generates a key pair and returns the public key. Optionally, the authenticator also returns an attestation to the identity provider such as Azure Active Directory.
The identity provider validates user identity and maps the public key to a user account during the registration or provisioning step. Authentication requires multiple factors, combining a key or certificate tied to a device and something that the person knows (a PIN) or something that the person is (biometrics). Private keys are securely stored on the device. Private keys are bound to a single device and never shared. These keys don’t roam and are never sent to external devices or servers.
This kind of authentication requires a local gesture. PIN entry and biometric gesture both trigger devices to use the private key to sign data that’s sent to the identity provider cryptographically. The identity provider verifies the user’s identity and authenticates the user.
Secure Authentication Flow Architecture
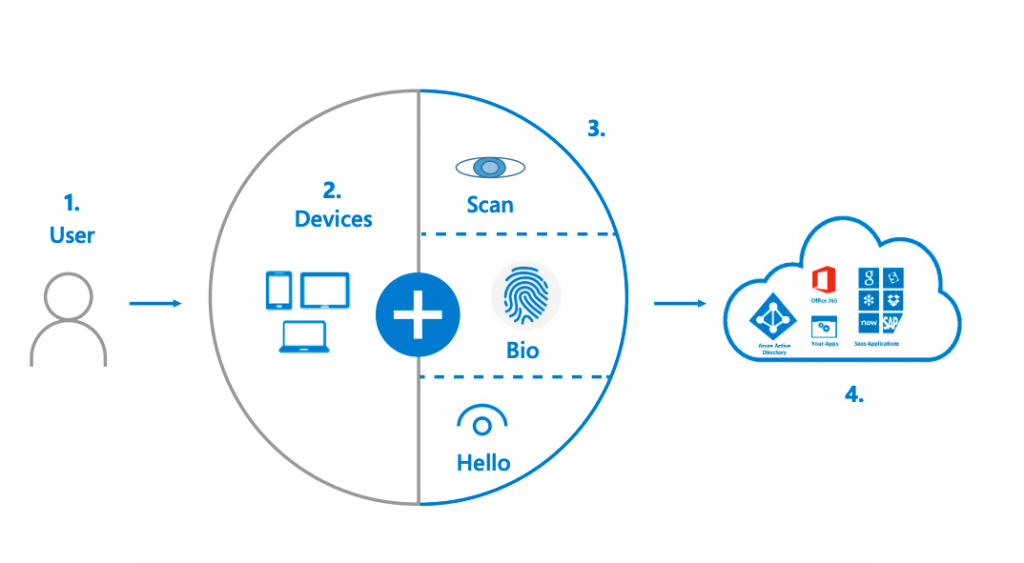
1. The user attempts to sign in to their account from a device. The device sends an authentication request. The identity system (for example, Azure AD) requests validation.
2. The user interacts with a local gesture (for example, biometric, PIN) from its device. The device uses the private key to sign nonce and returns to Azure AD with key ID. A request/signature containing both the nonce + the key ID signed with the device key sent to Azure AD.
3. Azure AD verifies the signature with the public key in the user object and verifies nonce. It builds a Primary Refresh Token (SSO token) and an ID token and sends them back along with an encrypted session key. The user accesses applications without the need for authenticating again (SSO).
Key Consideration #3: Driving User Adoption
No change is easy. All organizations face cultural and technical challenges as they move toward adopting password-less authentication methods.
While password-less authentication offers improved security and user experience, most organizations need to make some fundamental fixes to start on this journey. These fixes can be implemented over time to select groups to reduce your risk of attacks and security breaches.
All this effort, however, will pay off. From a technological viewpoint, reducing the use of passwords (and eventually eliminating them) can help you make a significant change in both security and productivity for your organization.
Getting rid of passwords can help you enjoy these benefits:
- As a user, you can sign in faster to use applications and services. There are no passwords to create, store, or remember.
- You don’t have to store passwords. Password-less authentication delivers a higher degree of trust and security for apps, devices, and service providers.
- It’s cost-effective for IT. IT support teams can be freed from endless password problems.
Overcoming the Old-School Mentality
It’s nearly impossible for an organization to visualize how different individuals go about their day-to-day activities, but it’s crucial for organizations to do just that. Understand that you’re encouraging people—including many in IT leadership—to switch from a widely adopted security system that’s very familiar, comfortable, and conventional. And don’t forget: change for most people is hard.
Yet, in this case, once users experience password replacements, they’ll forget that they even needed to enter passwords on a day-to-day basis or reset passwords on their own in a self-service portal. You can help them realize a password-less approach is simpler and better, and help them erase the mentality that passwords are the key to their world. Passwords are not enough anymore. It’s time to go to the next level of authentication.
Educating Users on New Authentication Methods
User acceptance is critical for the successful evolution of password-less authentication. An awareness drive on these new password-less authentication methods can help users understand and affirm the new way of authenticating to their devices, such as using Windows Hello for Business or Microsoft Authenticator-based applications.
Organizations need to educate their users that:
- Hackers easily guess passwords.
- Companies that have experienced data breaches may have leaked user data to the web. Hackers that obtain user information can use that information to guess further passwords because users often use the same (or a derivative) password for several sites or services.
- Phishing efforts often lead users to sign in to fake sites, giving their usernames and passwords away. With password-less authentication, this is an issue of the past because the physical keys are bound to the machines they use and FIDO2 tokens will not authenticate with a website it doesn’t trust.
A well-presented awareness practice will answer objections, encourage questions and feedback, and explain the value of this change, inspiring users to try it out.
Password-less Protection Takes Time—Start Now
The adoption of modern multi-factor authentication technologies—like biometrics and public-key cryptography in widely accessible devices—is one of the most impactful steps that can meaningfully reduce a company’s identity risk.
Given emerging requirements, organizations can prepare themselves by making a plan to start moving to password-less technologies. Going password-less is a long-term approach for secure authentication, and it’s still evolving. It can take time to transition.
You can start with a pilot of one or more options. For users that can’t go password-less, turn on MFA to validate users and minimize prompts based on the risk of the sign-in with conditional access capabilities. Use a password filter to block leaked credentials and common passwords from being used with password protection policies.
Not Sure Where to Start?
Initiating a foundational shift in your approach to security is a daunting task. A good first step toward ensuring you have a solid foundation of security is to participate in a Microsoft Security Assessment Workshop.
This workshop is an immersive, hands-on experience designed for security leaders. The workshop will identify your organization’s most pressing security risks and develop a plan to strengthen your approach to secure identities, data, applications, devices, and infrastructure.
Read the original article here
Check out their profile on CollabHub here


